IT security prepackaged rule sets
Setup an automate and revision-safe IT security verification audit with thousands of predefined rules in under 10 minutes
Use prepacked IT security rule sets for indivdual usage scenarios
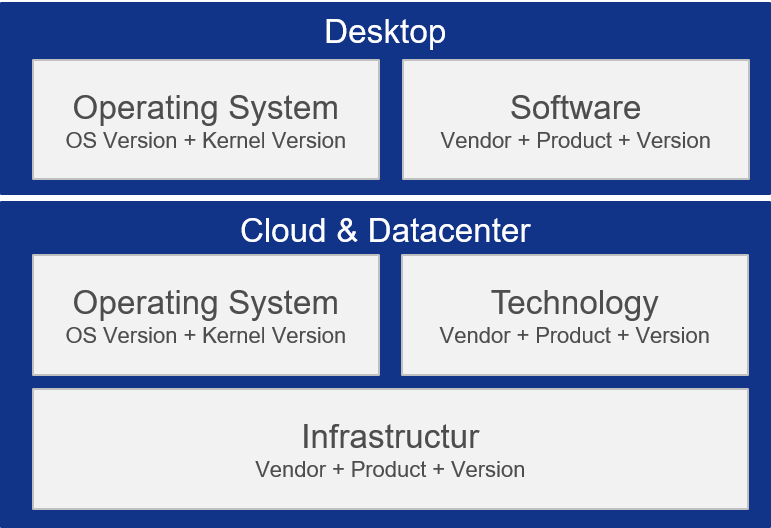
Use prepacked IT security rule sets for indivdual usage scenarios
With the prepackaged and continuously updated IT security rule packages of Versio.io you can fast and efficiently establish an auditable security audit process.
The Versio.io IT security rules based the national vulnerable database (NVD) by the National Institute of Standards and Technology (NIST).
Separate rule set packages for desktop, cloud and data center environments and infrastructure components enable the implementation of individual operational scenarios.
Start your IT security audit with thousands of predefined rules in under 10 minutes
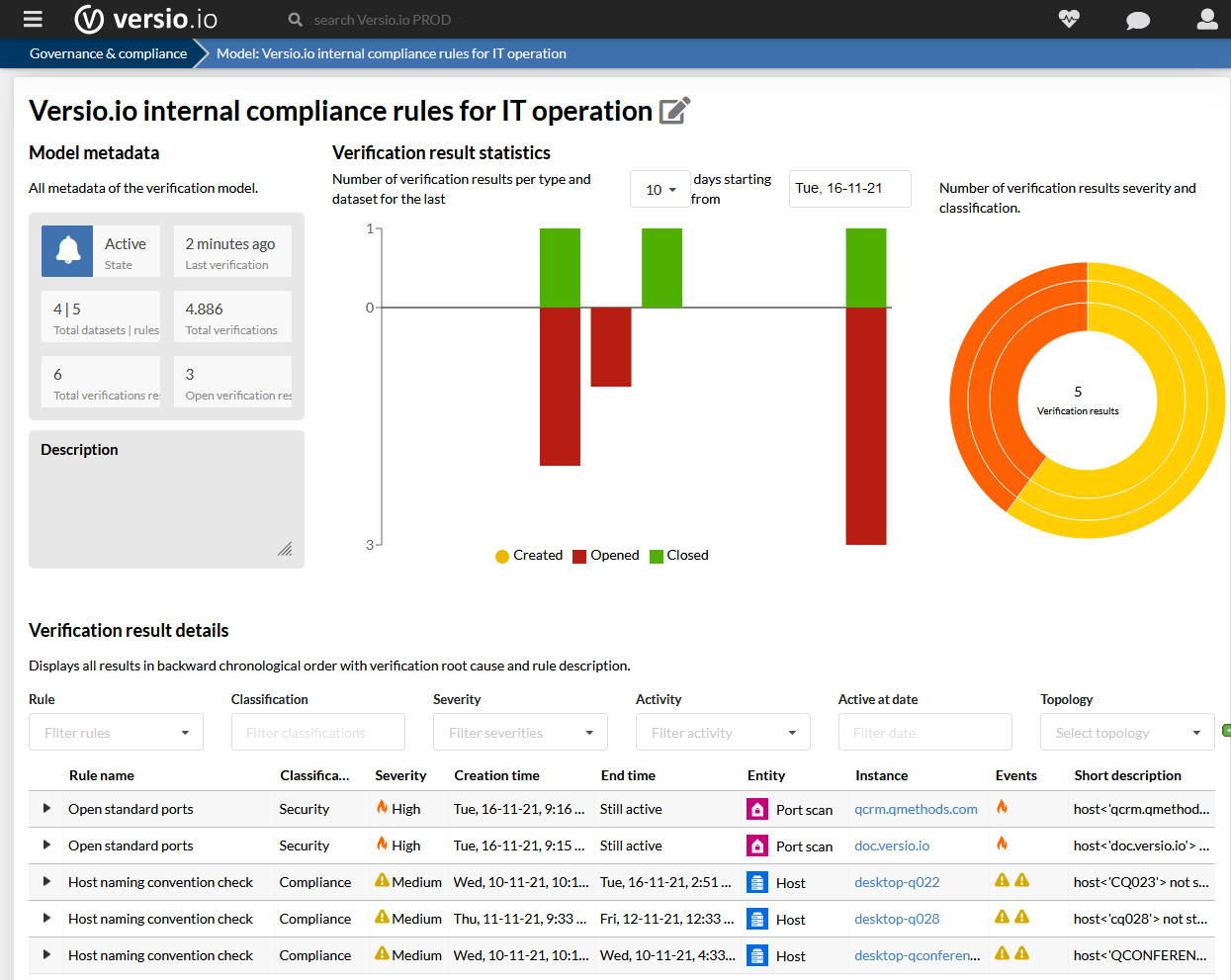
Start your IT security audit with thousands of predefined rules in under 10 minutes
Our solution enables you to automatically evaluate whether your data comply with the National Vulnaerability Database (NVD) by the National Insitute of Standards and Technology (NIST).
The NVD is the U.S. government repository of standards-based vulnerability management data and includes security checklists, security related software flaws, misconfigurations, product names, and impact metrics.
IT security vulnaerability description & violation root cause
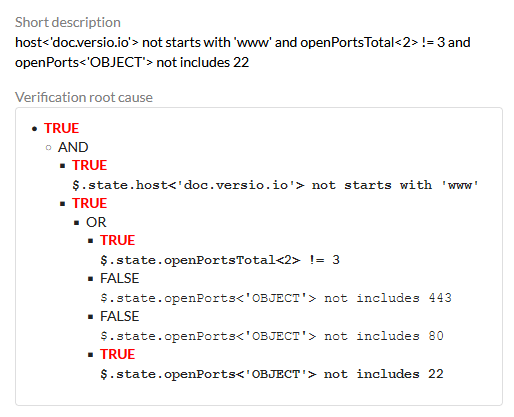
IT security vulnaerability description & violation root cause
Identified violations are documented in the form of verification results and events in an audit-proof manner.
Violation result and related events can trigger further actions like e-mail or chat notification, execution of IT operations cookbooks, creation of monitoring events, etc.
Keywords

