 The protection requirements analysis is a part of the IT security concept according
to the IT basic protection (German Federal Office for Information Security).
Here, the protection requirements of business processes and applications are defined
in the form of a protection requirements assessment.
The protection requirement of each IT component involved is derived by inheriting
the protection requirement determination.
This blog article describes an approach that customers can use to efficiently integrate
their protection requirement assessments into their IT service management and automatically
derive protection requirements for any IT components.
The protection requirements analysis is a part of the IT security concept according
to the IT basic protection (German Federal Office for Information Security).
Here, the protection requirements of business processes and applications are defined
in the form of a protection requirements assessment.
The protection requirement of each IT component involved is derived by inheriting
the protection requirement determination.
This blog article describes an approach that customers can use to efficiently integrate
their protection requirement assessments into their IT service management and automatically
derive protection requirements for any IT components.
Automated determination of the protection requirements
Aggregation of protection requirements through inheritance of protection requirement assessments for each IT component
In a nutshell Request demo Free trial The protection requirements analysis is a part of the IT security concept according
to the IT basic protection (German Federal Office for Information Security).
Here, the protection requirements of business processes and applications are defined
in the form of a protection requirements assessment.
The protection requirement of each IT component involved is derived by inheriting
the protection requirement determination.
This blog article describes an approach that customers can use to efficiently integrate
their protection requirement assessments into their IT service management and automatically
derive protection requirements for any IT components.
The protection requirements analysis is a part of the IT security concept according
to the IT basic protection (German Federal Office for Information Security).
Here, the protection requirements of business processes and applications are defined
in the form of a protection requirements assessment.
The protection requirement of each IT component involved is derived by inheriting
the protection requirement determination.
This blog article describes an approach that customers can use to efficiently integrate
their protection requirement assessments into their IT service management and automatically
derive protection requirements for any IT components.
Protection requirement assessments become part of the IT landscape
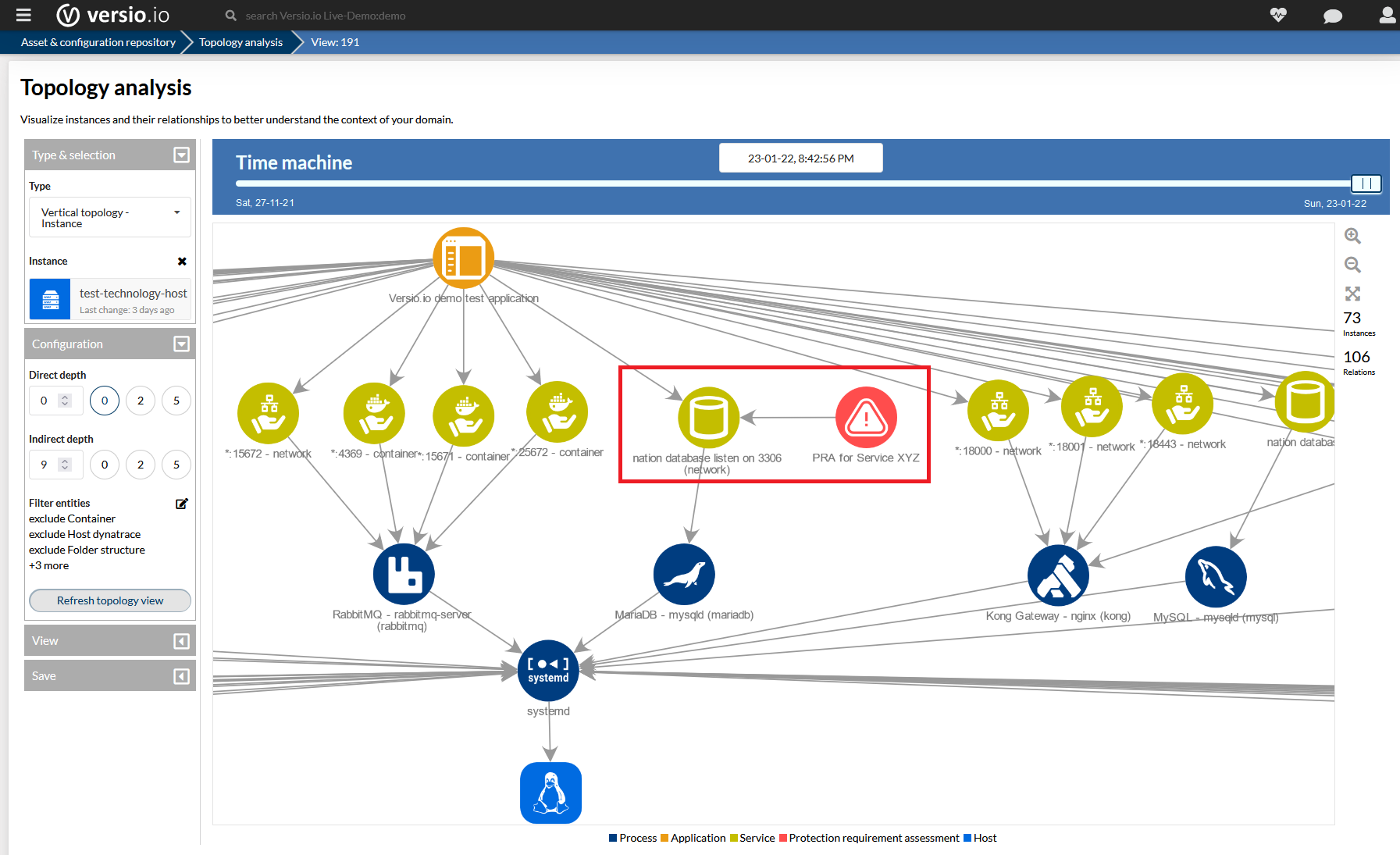
Protection requirement assessments become part of the IT landscape
Versio.io allows you to capture and edit protection requirements or import them from third-party systems.
In Versio.io, protection requirements are directly related to the target object to be protected. Thus, the protection requirements become part of the IT infrastructure and application landscape (topology) and thus part of the daily operational work processes.
The figure shows a protection requirements assessment (PRA in red), which directly references the IT service (database 'nation').
Aggregate protection requirements for component of the IT landscape through inheritance
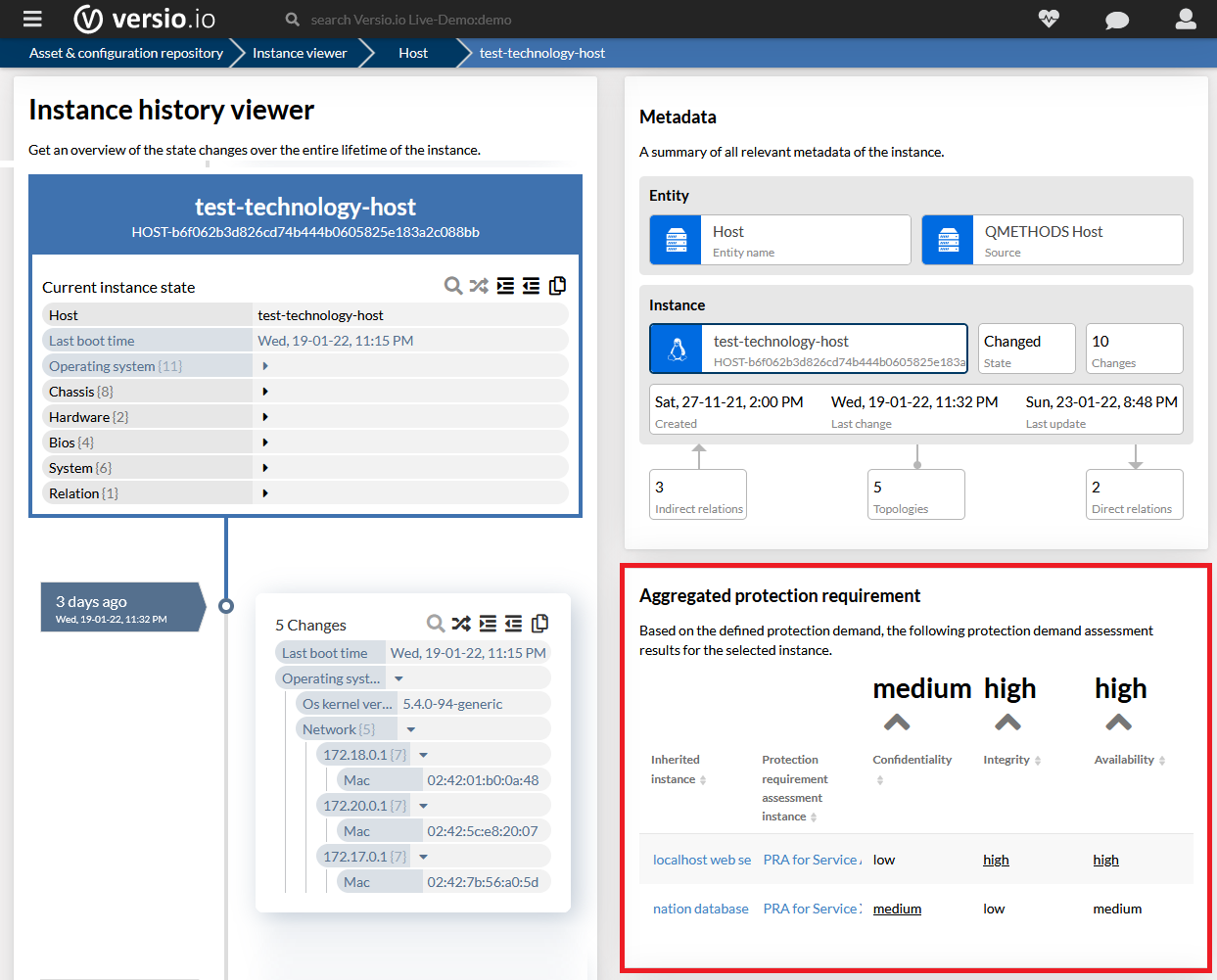
Aggregate protection requirements for component of the IT landscape through inheritance
For each individual structural element of the IT infrastructure and application landscape, the specific protection requirements must be determined on the basis of the existing protection requirements.
Versio.io determines the protection requirements for each structural element depending on the existing protection requirements based on inheritance methods (maximum, dependency, accumulation, distribution).
The figure shows a host computer that is affected by two related protection requirements and the resulting aggregated protection requirement for the host computer.
Efficient management & use of protection requirements assessment with Versio.io
- Information basis for structural analysis - Versio.io uses the asset & configuration repository to provide all the information for the initial structural analysis as part of the protection requirements assessment in the form of data, processes, IT systems, applications, rooms and communication links to be considered.
- Management or integration of protection requirement assessments - Versio.io allows you to capture and edit protection requirement assessments or import them from third-party systems.
- Change management of protection requirement assessments - Versio.io detects changes in protection requirement assessments and historizes them in an automated and audit-proof manner.
- Determination of the protection requirement - Versio.io determines the protection requirements for each structural element depending on the existing protection requirements assessment according to different inheritance methods (maximum, dependency, accumulation, distribution).
- Compliance of protection requirement assessments - Each change to a protection requirement assessments statement can be verified for content (naming convention, completeness, etc.).
- Simulation of the impact of protection requirement assessments - Determine the impact of new or modified protection requirements on structural elements.
- Determination of cost optimization by means of inherited protection requirements - Identification of cost optimization based on inherited protection requirements and potential operational adaptation of structural elements (e.g. database management systems, virtualization platforms, etc.).
Read more

Governance policy compliance
The Versio.io IT governance solution supports companies to formalise compliance with internal and regulatory requirements and automate their monitoring. All breaches are mapped in the risk matrix depending on the protection requirement assessment.

Asset & configuration inventory
Versio.io offers a central asset & configuration inventory with automated full-stack detection for your infrastructure, application and organisation landscape. This digital twin enables more efficient DevSecOps and IT operations.
Talk to us


Keywords


