Network infrastructure management
Inventory and manage routers, switches, firewalls & network attached storages
In a nutshell Request demo Free trialSupported vendor integrations
Deep insights into your IT network
Versio.io inventories a 100% digital twin of your physical network device or virtual network appliance
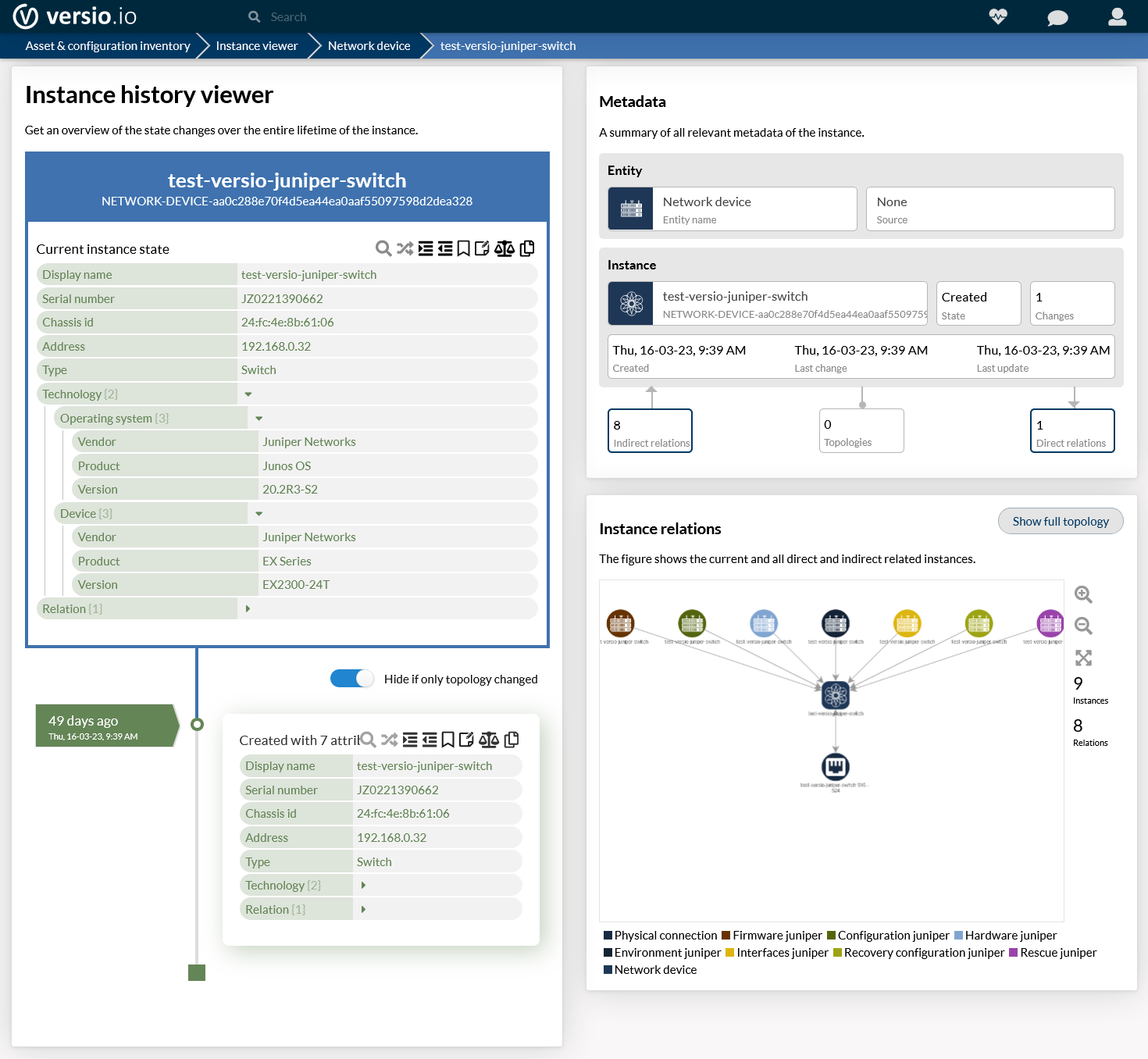
Versio.io inventories a 100% digital twin of your physical network device or virtual network appliance
Versio.io continuously inventories all your network devices so that you always have the current configuration of the network device available in Versio.io.
We call it a digital twin - an image of reality. This makes it easier for you to access the configurations of the network devices and enables downstream processing in terms of correct change request execution, release & patch assessment, security assessment, IT governance compliance, etc..
Centralis events from network devices and use of powerful analysis and alerting

Centralis events from network devices and use of powerful analysis and alerting
The centralised recording of business-relevant events makes it possible to efficiently control extensive network device landscapes and manufacturer production facilities.
Analyses can be made on the basis of the layers listed below and enable a quick overview of risks and criticality in the mass of possible events:
- Event source
- Severity
- Classification
- Entity
- Instance
- Protection requirement
- OneGate
Check the status of network devices using rule-based guidelines - day and night!
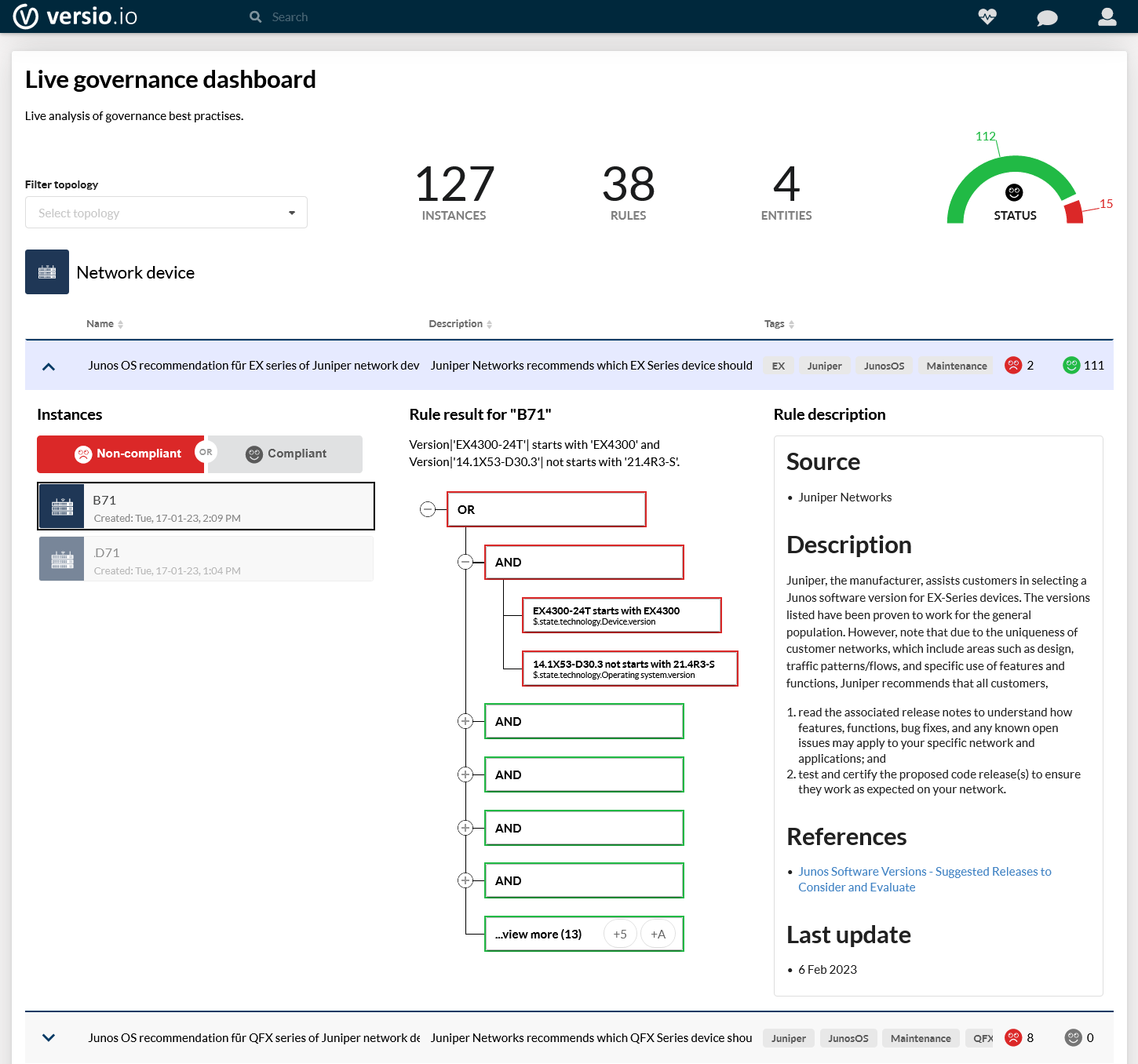
Check the status of network devices using rule-based guidelines - day and night!
Based on the inventoried network device configurations, you can define and execute freely definable verifications in the form of rules to ensure compliance with internal and regulatory requirements.
The example shows an IT governance check whether the network devices used use the operating system version recommended by the manufacturer depending on the model.
Automated monitoring of the lifecycle and security status of network devices to prevent cyberattacks
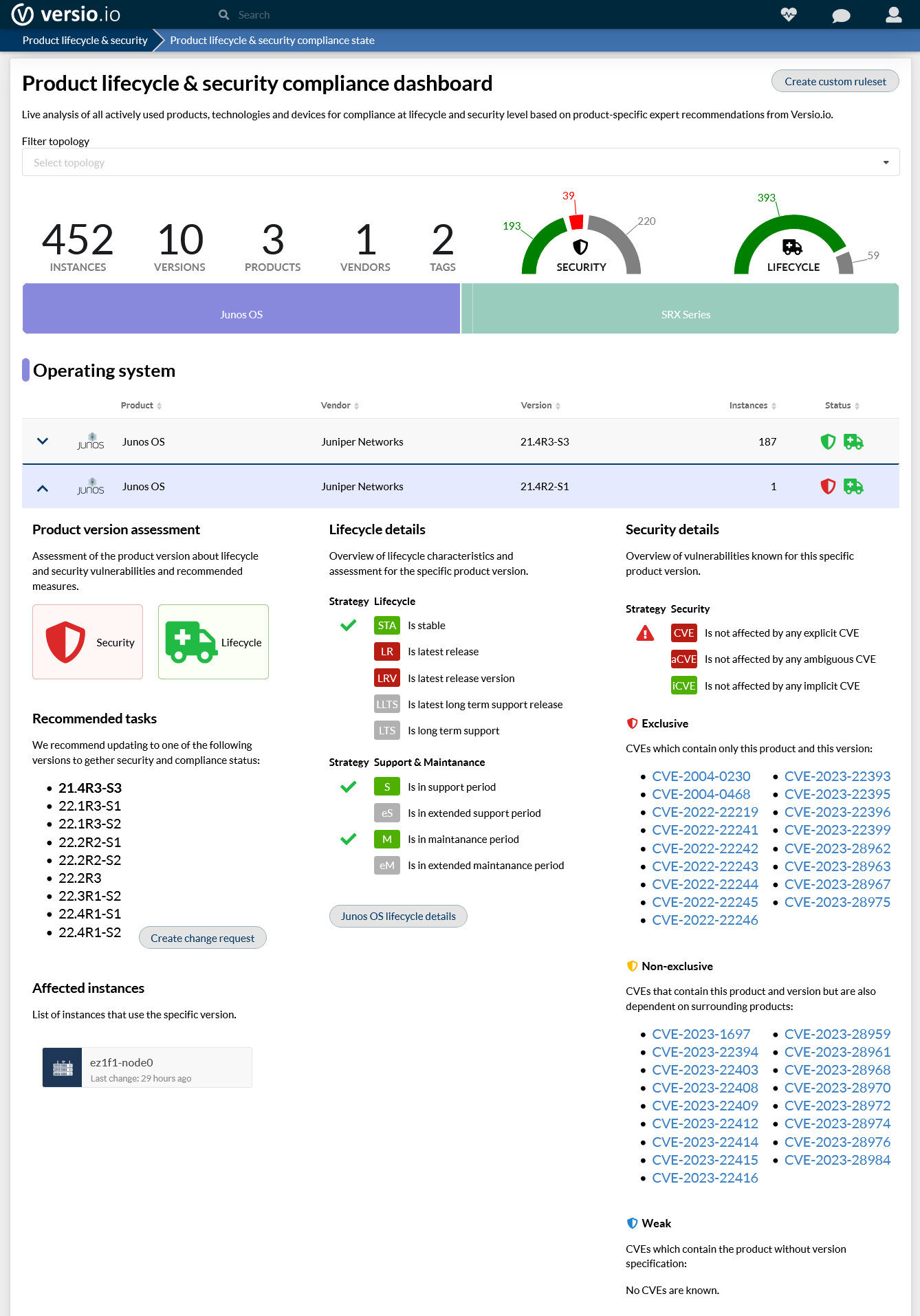
Automated monitoring of the lifecycle and security status of network devices to prevent cyberattacks
Based on the operating system version of the network device, the up-to-dateness of the operating system version can be checked according to internal release and patch specifications and the presence of known security vulnerabilities for the version used can be detected.
This assessment enables you to always keep your IT landscape up to date and secure. Automate the EOL and vulnerability detection and focus your activity on the decision depending on your company-specific situation.
Physical and logical network plans help you to act in a network context
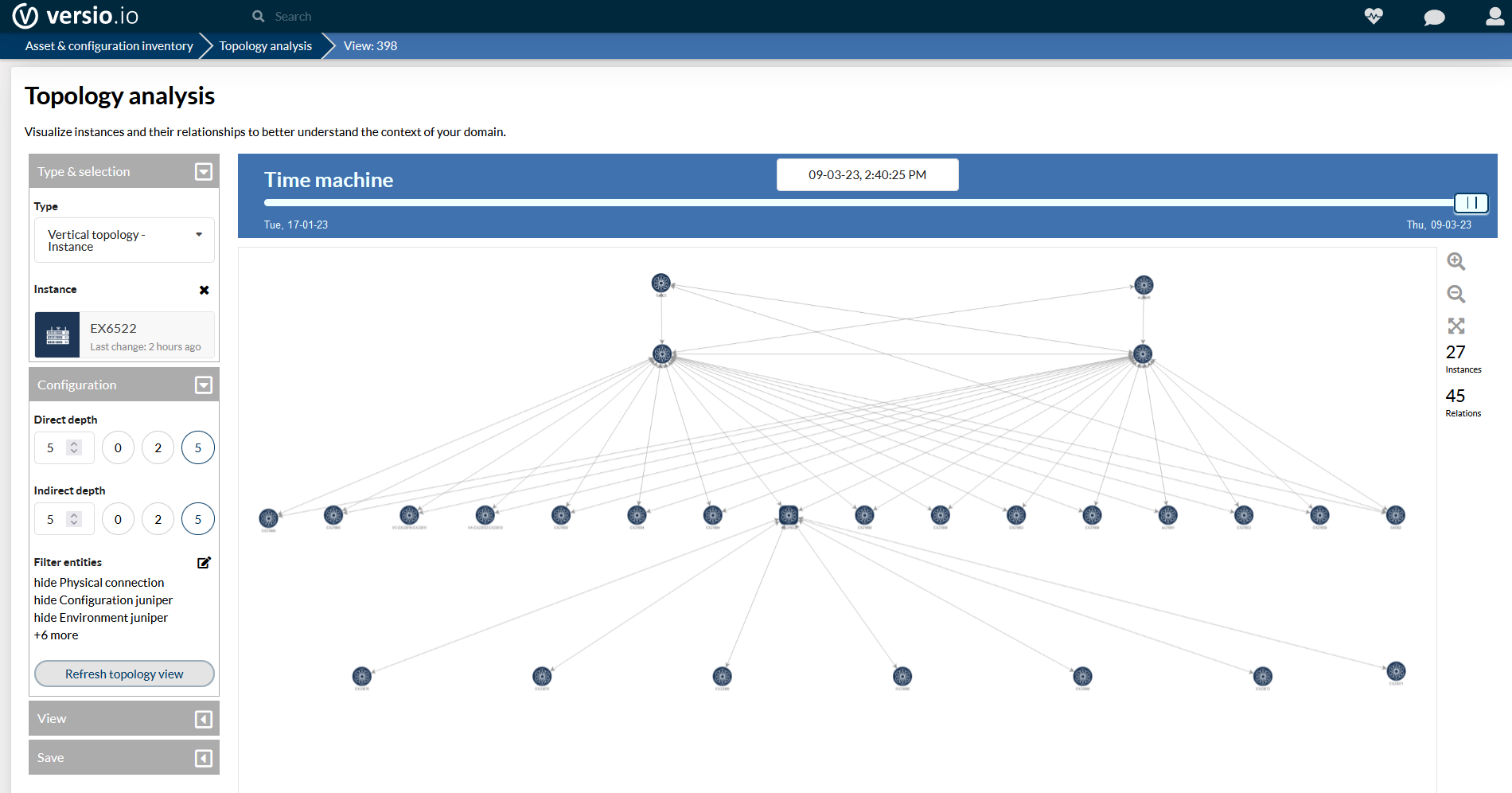
Physical and logical network plans help you to act in a network context
An important step in planning and optimizing a network is to have a network map that shows the physical and logical connections between the various network devices such as routers, switches, servers and end devices. Such a network map can be detect by Versio.io 100% automatically and visualize the detected relationships between all devices. By looking at the network map, one can better understand the topology, configuration, performance, and security of the network and identify potential problems or opportunities for improvement.
Use scenarios with added value
- Inventory (CMDB) - Central and historized inventory over all network device configurations
- Event management - Centralised analysis and alerting of all event messages from network devices (SNMP trap, syslog)
- Network plan - Detect and visualize the physical and logical structure of network device topologies
- Change detection - Detect changes to network device configurations or network cabling
- Change request execution monitoring - Live monitoring and auto documentation of network device change request
- Recovery - Recovery a previous network device configuration
- Analyzing & reporting - Analyse and report network device data
- Release & patch management - Detect network devices with outdated software versions or software versions without maintenance and support
- Vulnerability detection - Detect network devices with known security vulnerabilities
- IT governance - Verify network device configurations with respect to antipattern (bad or error-prone configurations)
Read more

Asset & configuration inventory
Versio.io offers a central asset & configuration inventory with automated full-stack detection for your infrastructure, application and organisation landscape. This digital twin enables more efficient DevSecOps and IT operations.

Event management
Versio.io event Management enables you to centrally record and analyse events from the IT landscape, third-party applications and OT/IoT devices from production facilities.

Product lifecycle & vulnerability
With the product lifecycle & vulnerability solution, Versio.io supports customers in evaluating used hardware and software products with regard to their lifecycle and known security vulnerabilities on the basis of the detected version.
Talk to us


Keywords


