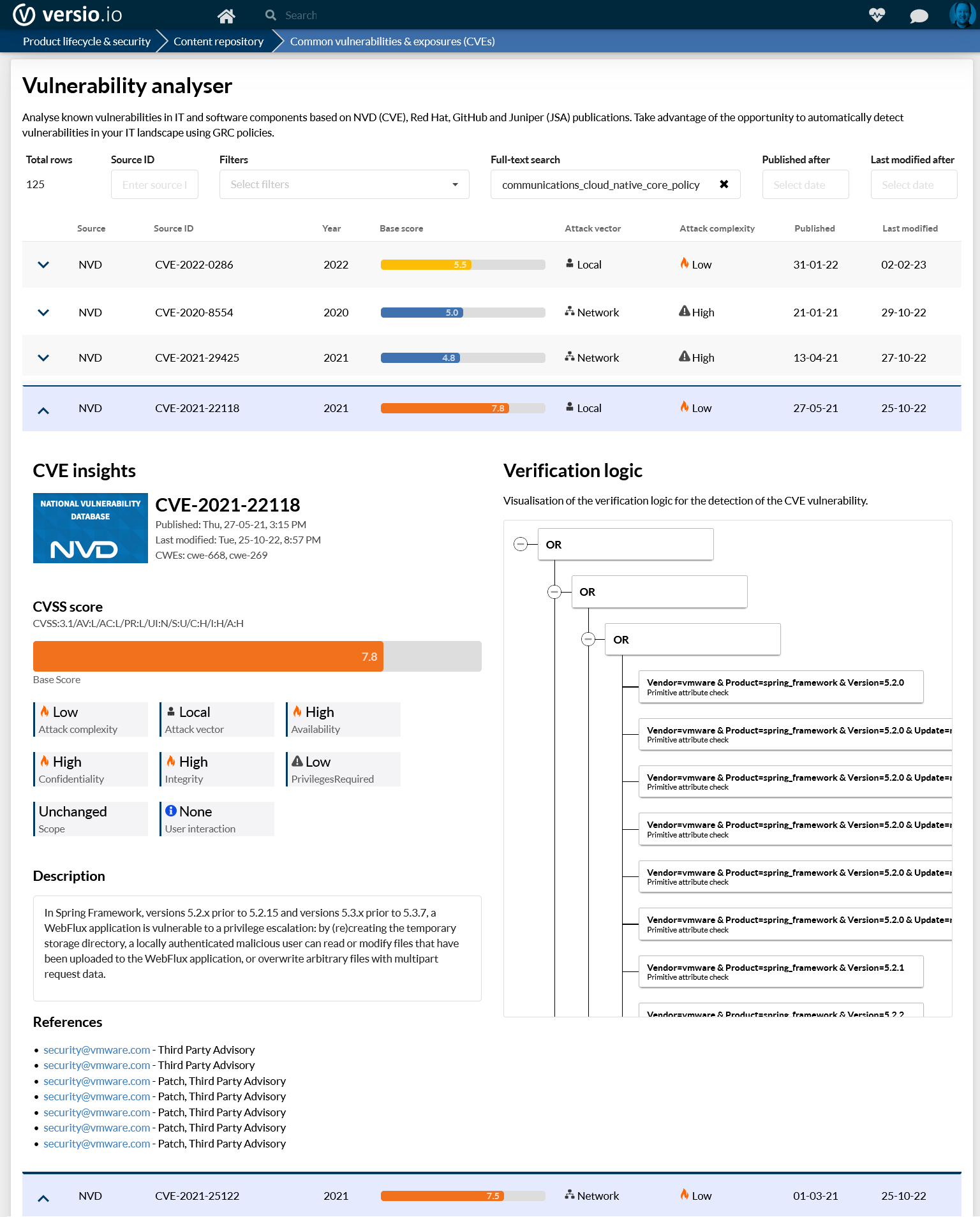
Common vulnerabilities & exposures database (CVE)
Consolidated and centralised access to hardware and software product release information on enterprise level
Consolidated and centralised access to hardware and software product release information on enterprise level
Versio.io offers enterprise customers a common vulnerabilities & exposures database for hardware and software products.
Here, Versio.io imports new or changing CVEs from various CVE vendors and manufacturers on a daily basis.
The following advantages result for customers by using the Versio.io CVE database:
- Centralized and daily updated database
- Harmonized and standardized data
- Alerting possibility for specific CVE (e.g. Red Hat Kernel or Tomcat security vulnerability)
- Generation of compliance rulesets for automated verification
- Change history over the entire lifecycle of a CVE
Read more

NIS2 Maßnahmen effizient und zeitnah operativ umsetzen 🇩🇪
Ihr Unternehmen ist verpflichtet, die NIS2-Richtlinie bis zum Oktober 2024 umzusetzen und Sie suchen noch nach Ansätzen, wie Sie NIS2 effizient und zeitnah operativ umsetzen können? Wir zeigen Ihnen Lösungsansätze mittels Versio.io auf.

Product lifecycle & vulnerability
With the product lifecycle & vulnerability solution, Versio.io supports customers in evaluating used hardware and software products with regard to their lifecycle and known security vulnerabilities on the basis of the detected version.

Content repository - product release & end-of-life
A daily updated, centralised and harmonised content repository of versions, releases and patches of software and hardware products as well as their end-of-life (maintenance, support) information.
Talk to us


Keywords

