
Risk management based on protection requirements
Use the potential of high-quality inventory data to optimise the IT infrastructure, technology used, service quality and support process
In a nutshell Request demo Free trialAnalyse violation of all Versio.io solutions
Analyse violation of all Versio.io solutions
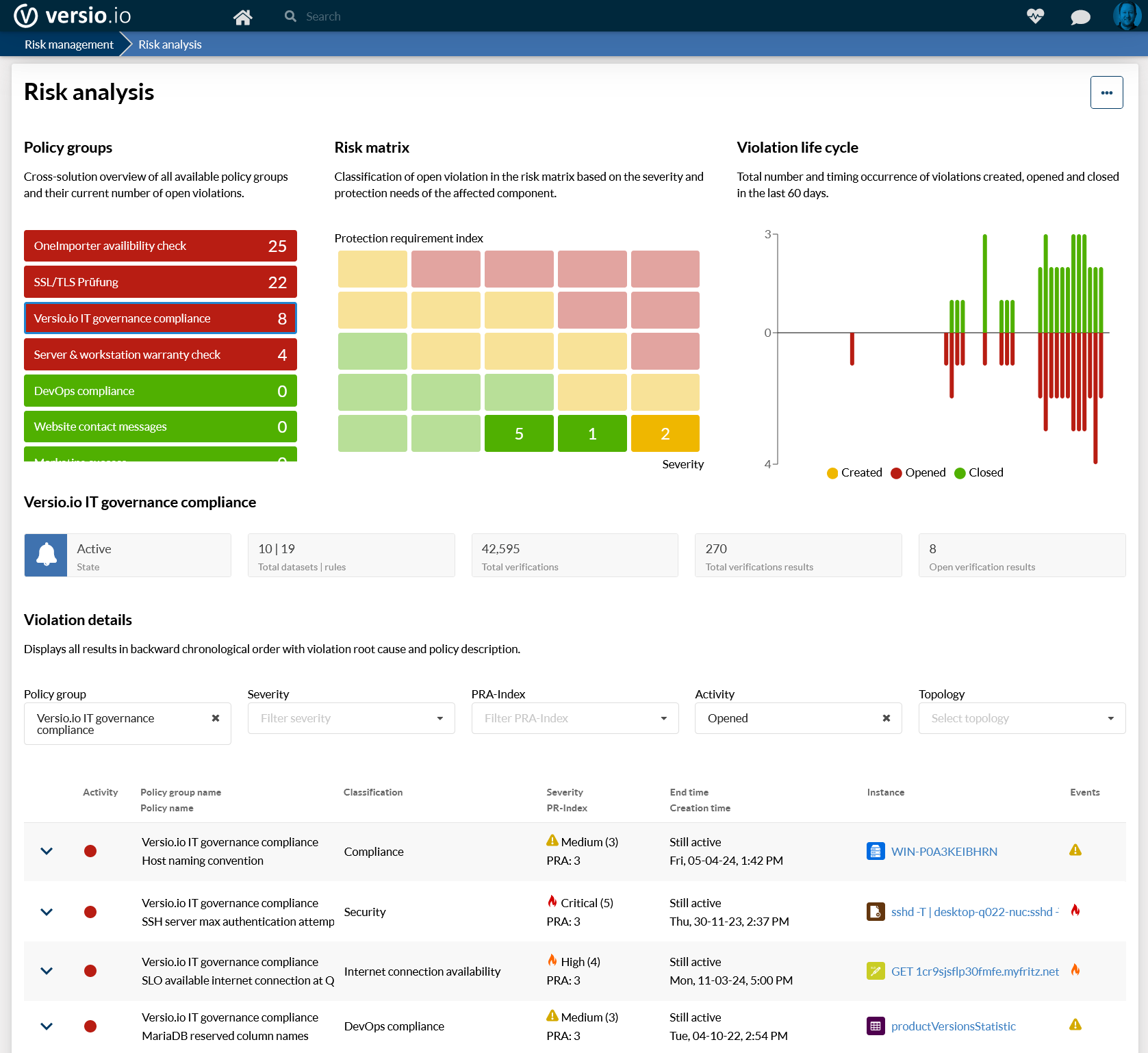
The Versio.io solutions automatically check the status of assets and configurations whenever they are changed. If internal and regulatory requirements have not been met, these are documented in the form of violations. The time at which the violation was identified and the time at which the problem was resolved is recorded with the violation. This provides audit-proof documentation of the IT team's ability to react.
Versio.io Risk Management provides an overview of all breaches. Powerful filter options make it possible to make the violations transparent according to different aspects and to recognise the operational sequence in which the causes of the problem are resolved.
Detailed documentation and links to further relevant information about the violation support you in analysing the causes.
Aggregate the protection requirements for each IT component through inheritance and use them to prioritise violations
Aggregate the protection requirements for each IT component through inheritance and use them to prioritise violations
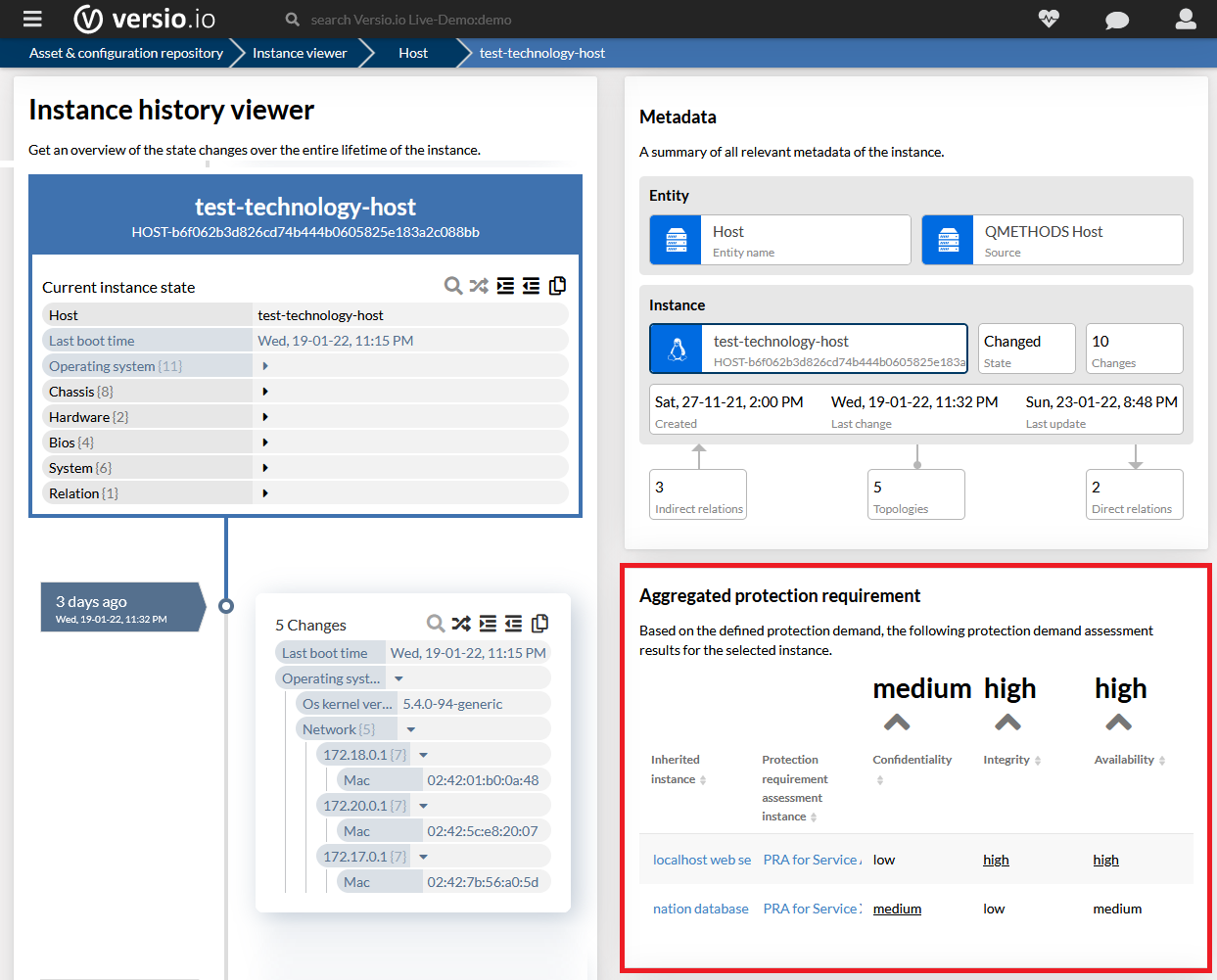
For each individual structural element of the IT infrastructure and application landscape, the specific protection requirements must be determined on the basis of the existing protection requirements.
Versio.io determines the protection requirements for each structural element depending on the existing protection requirements based on inheritance methods (maximum, dependency, accumulation, distribution).
The figure shows a host computer that is affected by two related protection requirements and the resulting aggregated protection requirement for the host computer.
Read more
Efficiently determine IT protection requirement
This blog article shows how protection requirement assessments can be efficiently integrated into ITSM and how protection needs for all IT components can be derived automatically.

NIS2 Maßnahmen effizient und zeitnah operativ umsetzen 🇩🇪
Ihr Unternehmen ist verpflichtet, die NIS2-Richtlinie bis zum Oktober 2024 umzusetzen und Sie suchen noch nach Ansätzen, wie Sie NIS2 effizient und zeitnah operativ umsetzen können? Wir zeigen Ihnen Lösungsansätze mittels Versio.io auf.

Governance policy compliance
The Versio.io IT governance solution supports companies to formalise compliance with internal and regulatory requirements and automate their monitoring. All breaches are mapped in the risk matrix depending on the protection requirement assessment.
Talk to us


Keywords

