 The security of IT systems must be re-evaluated each time there is a change in
the dynamic behaviour or the static state in order to avoid risks for IT and the company.
The following blog post shows how Versio.io can support you in ensuring IT security
in your company.
The security of IT systems must be re-evaluated each time there is a change in
the dynamic behaviour or the static state in order to avoid risks for IT and the company.
The following blog post shows how Versio.io can support you in ensuring IT security
in your company.
How can I improve IT security with Versio.io?
Automate the detection, documentation and verification of security-related changes
 The security of IT systems must be re-evaluated each time there is a change in
the dynamic behaviour or the static state in order to avoid risks for IT and the company.
The following blog post shows how Versio.io can support you in ensuring IT security
in your company.
The security of IT systems must be re-evaluated each time there is a change in
the dynamic behaviour or the static state in order to avoid risks for IT and the company.
The following blog post shows how Versio.io can support you in ensuring IT security
in your company.
Positioning of Versio.io in the IT security architecture
Pre-packaged IT security rules
Which data in Versio.io contains which security relevant information?
| Entity | Relevant attributes and relations | Security related detection of ... |
|---|---|---|
| General |
|
|
| Host |
|
|
| OS process |
|
|
|
SSL certificate
Whois Token |
|
|
| Port scan result |
|
|
| User & role |
|
|
| File configuration |
|
|
| Batch job |
|
|
Host port status as a practical example
Versio.io detects and documents changes on a port of a host
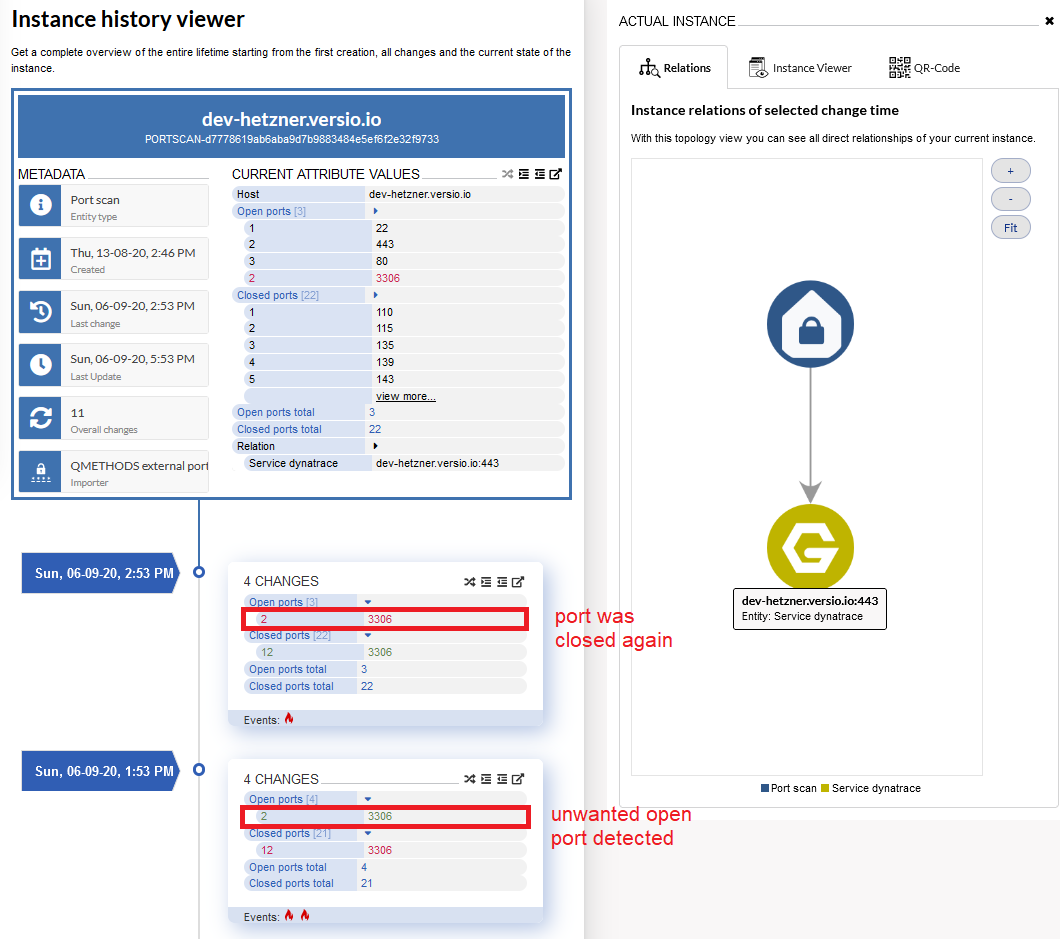
Versio.io detects and documents changes on a port of a host
The state of the host port is continuously monitored by the Versio.io OneImporter and transmitted to the Versio.io platform. The platform checks whether a change has been made and saves it. This creates an auditable and audit-proof database of all changes in your company.
In addition to the historical storage of instance changes in Versio.io, the relationships to other instances can also be identified. This is also possible to instances from other data sources and thus increases the possibilities to validate or process data depending on its context.
With an easy to define compliance rule in Versio.io the unwanted status of the change can be detected
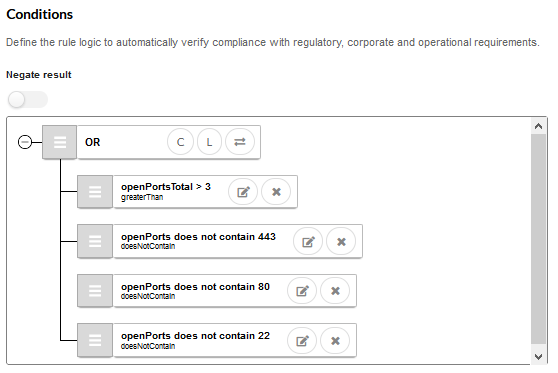
With an easy to define compliance rule in Versio.io the unwanted status of the change can be detected
With the visual rule editor, logical rules can be defined and executed based on the data imported into Versio.io. If the rule logic matches, a corresponding violation event is triggered.
The violation can also include the time from the identification of the violation to its removal. This documentation ensures auditability.
The identified change and the defined compliance rule lead to an event with a complete root cause analysis and corresponding actions
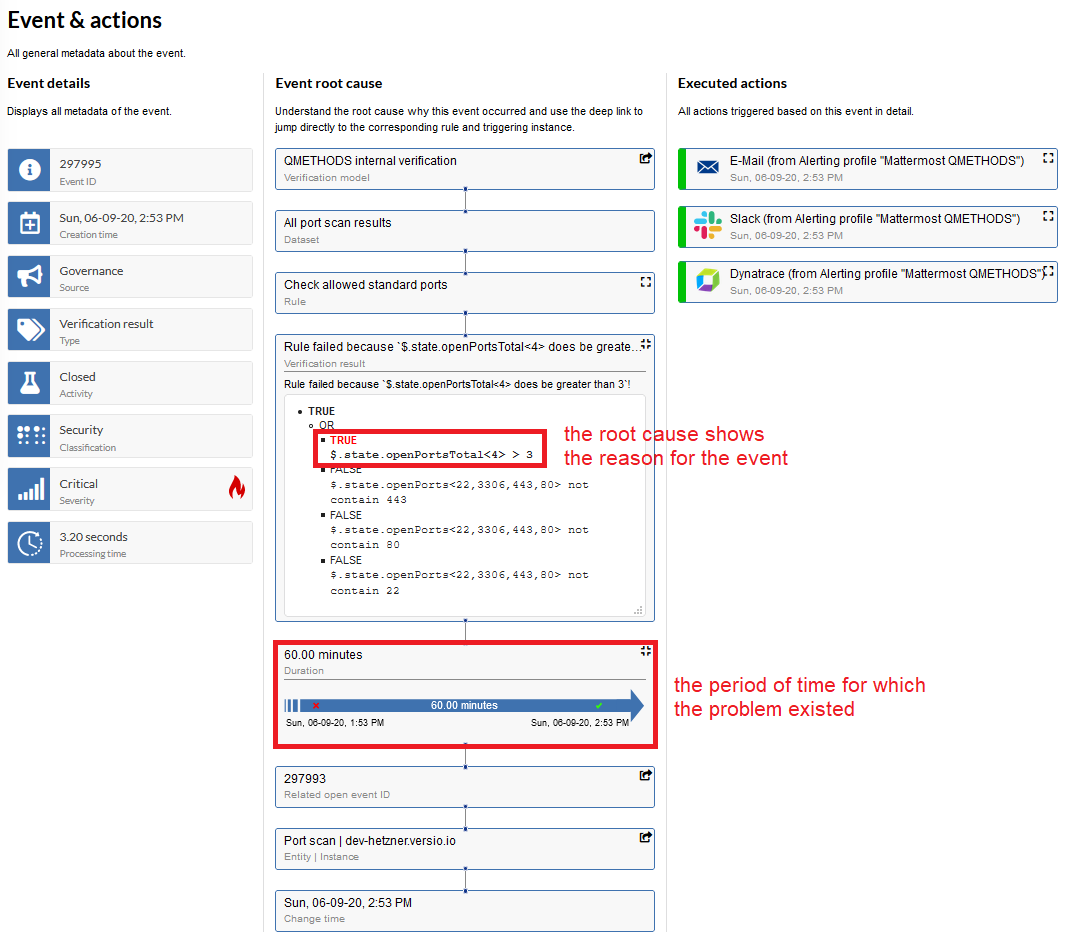
The identified change and the defined compliance rule lead to an event with a complete root cause analysis and corresponding actions
The compliance violation event provides all necessary information about the event.
We are especially proud of the root cause display, which gives you all the details about the root cause of the problem, the duration of its existence, a direct link to the causing instance and actions triggered by the event.
Related references
Keywords


